Computer viruses are malicious programs designed to spread and infect computer systems, causing a range of damaging effects from data corruption to system failure. With the ever-evolving landscape of technology, the threat of dangerous computer viruses has grown exponentially. One of the most notorious viruses in history, the “ILOVEYOU” virus, emerged in 2000, spreading rapidly…
Category: Security
18 Ways Remote Access Software Can Improve an IT Projects
How Remote Access Software can save time, energy, and money while enhancing security? Remote access software has revolutionized the way businesses operate, offering a myriad of benefits that can significantly impact efficiency, cost-effectiveness, and security. There are several ways Remote Access Software can improve your IT Projects. By enabling employees to access their workstations and…

14 Top Benefits of Cloud-Based Master Data Management
What are the benefits of cloud-based master data management? Cloud-based master data management (MDM) offers a myriad of benefits to organizations seeking efficient and scalable data governance solutions. By centralizing critical data assets in a secure cloud environment, businesses can streamline their operations, enhance decision-making processes, and achieve greater agility in adapting to evolving market…

15 Data Protection Tips To Secure Google Drive from Hackers
What are some useful tips to secure Google Drive from others as well as from hackers? Securing your Google Drive from hackers is paramount to safeguarding your sensitive information and maintaining your privacy. With the increasing prevalence of cyber threats, it’s crucial to implement robust security measures to protect your data stored in the cloud….

16 Secured Ways To Protect Enterprise Data From USB Drives
What are some secured ways to protect enterprise data from USB Drives? In today’s digital landscape, safeguarding enterprise data from potential threats is paramount. One significant vulnerability lies in the ubiquitous USB drives, which can inadvertently introduce malicious software or lead to data breaches if mishandled. To protect sensitive information, robust measures must be implemented…

44 Electrical Safety Symbols Signs: Meaning, Download PDF
In the contemporary epoch, we find ourselves immersed in the marvels of technology, an era where the ubiquitous presence of technological advancements has become an integral facet of our daily lives. From the crackling of the first telegraph to the seamless transmission of information through the internet, the pace of technological evolution has been nothing…
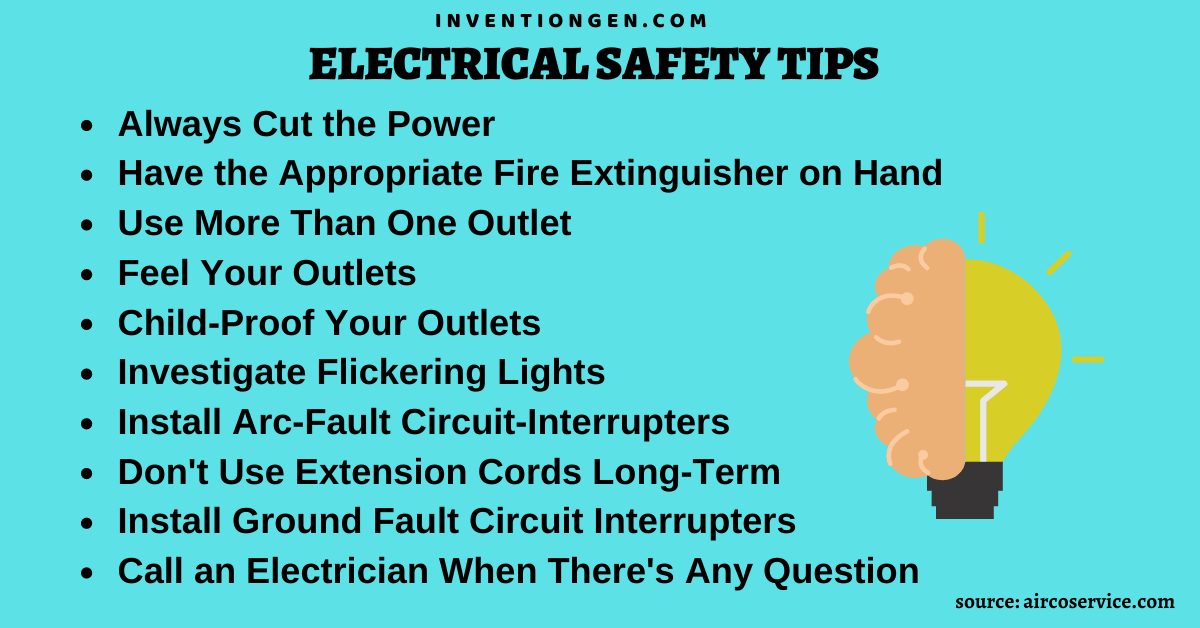
50 Electrical Safety Tips: Home, Appliances, Work, Industries
Electricity plays a pivotal role in our daily lives, powering essential appliances and devices that enhance our comfort, productivity, and overall well-being. From lighting our homes to fueling electronic gadgets, electrical items are integral to modern living. The convenience they offer is undeniable, making tasks more efficient and enjoyable. However, with this convenience comes a…

Create a Secured Remote Work Online: Why and How
Why and how to create a secured remote work online? For some, working from home has long been an integral aspect of their job, while others are still adapting to this novel work environment. A survey by Owl Labs illuminates the appeal of remote work, with 46 percent of employees expressing their willingness to accept…

4 Tips to Remove Personal Information from Internet Sources
What are some of the smart tips to remove personal information from internet sources? Regrettably, there’s no foolproof way to ensure the complete elimination of all online data tied to an individual. However, one can take measures to minimize their digital footprint, including deleting social media and email accounts, contacting website administrators to request data…

What Is Shoulder Surfing and How Do You Prevent It?
What is shoulder surfing and how do you prevent it? In the fast-paced and interconnected world of today, technology assumes an indispensable role in the lives of individuals, highlighting the pressing need to safeguard one’s personal information. With people increasingly conducting various tasks on their electronic devices, from sharing sensitive data to conducting financial transactions,…
